|
|
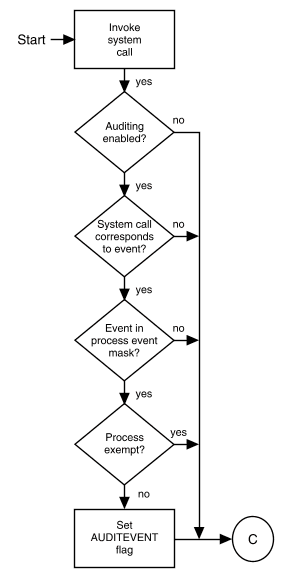
``Auditing algorithm'' illustrates how the event masks are used to determine when to generate an audit record for an event:

Auditing algorithm
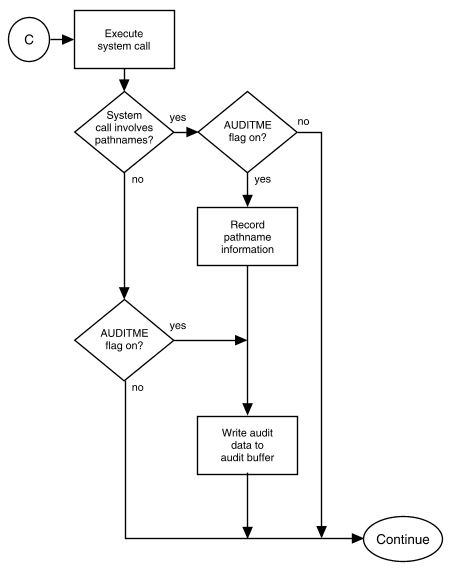
Auditing algorithm (cont)
Whenever a system call is invoked, the kernel invokes the systrap routine to perform system call processing. This routine is also used to check if the system call being executed represents an auditable event. The checks are made as follows:
For efficiency, the auditing subsystem records much of its data in numeric format. The audit record is usually written to one of a number of audit buffers in the kernel. The tunable parameter ADT_NBUF controls the number of audit buffers in the kernel and ADT_BSIZE controls the size of each of the buffers. The tunable parameter ADT_LWP_BSIZE controls the size of the per-LWP audit buffer in multiprocessor systems. These are defined in the /etc/conf/mtune.d/audit file.
The high water mark controls the amount of data stored in an audit buffer before auditing switches to the next available buffer. Whenever an audit record would make the amount of data in a buffer larger than the high water mark the auditing subsystem flags the buffer as writable and switches to a new buffer. It also awakens the audit daemon process which will write the flagged buffer to the audit event log file and returns the buffer to the pool of available buffers. If all available buffers are full, the process that is generating the audit record sleeps until a buffer becomes available.